Information Security Risk Assessment
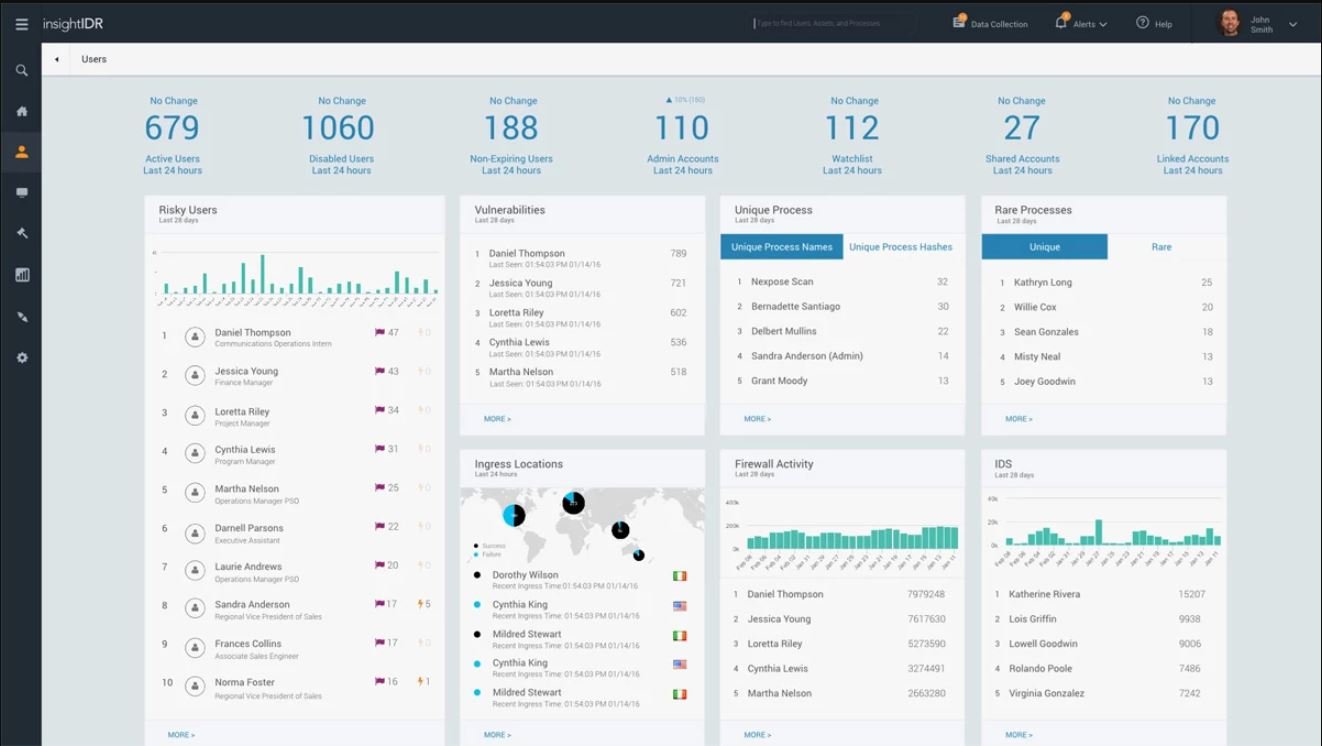
Using the Metasploit tool, it is possible to detect and take action against vulnerable users in the organization's network and software based on artificial intelligence.
Using the Metasploit tool, it is possible to detect and take action against vulnerable users in the organization's network and software based on artificial intelligence.
Vulnerability Management Features
Automatically assess and understand risk across your entire infrastructure
-
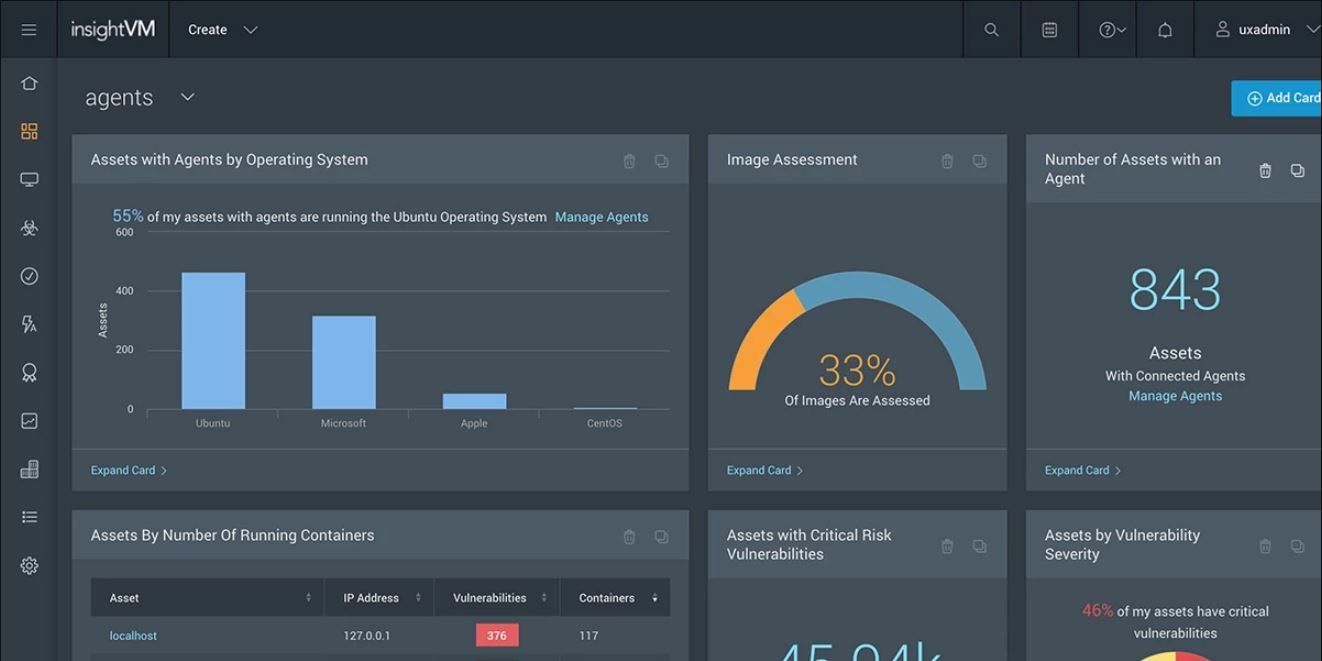
Lightweight Endpoint Agent
-
Live Dashboards
-
Active Risk Score
-
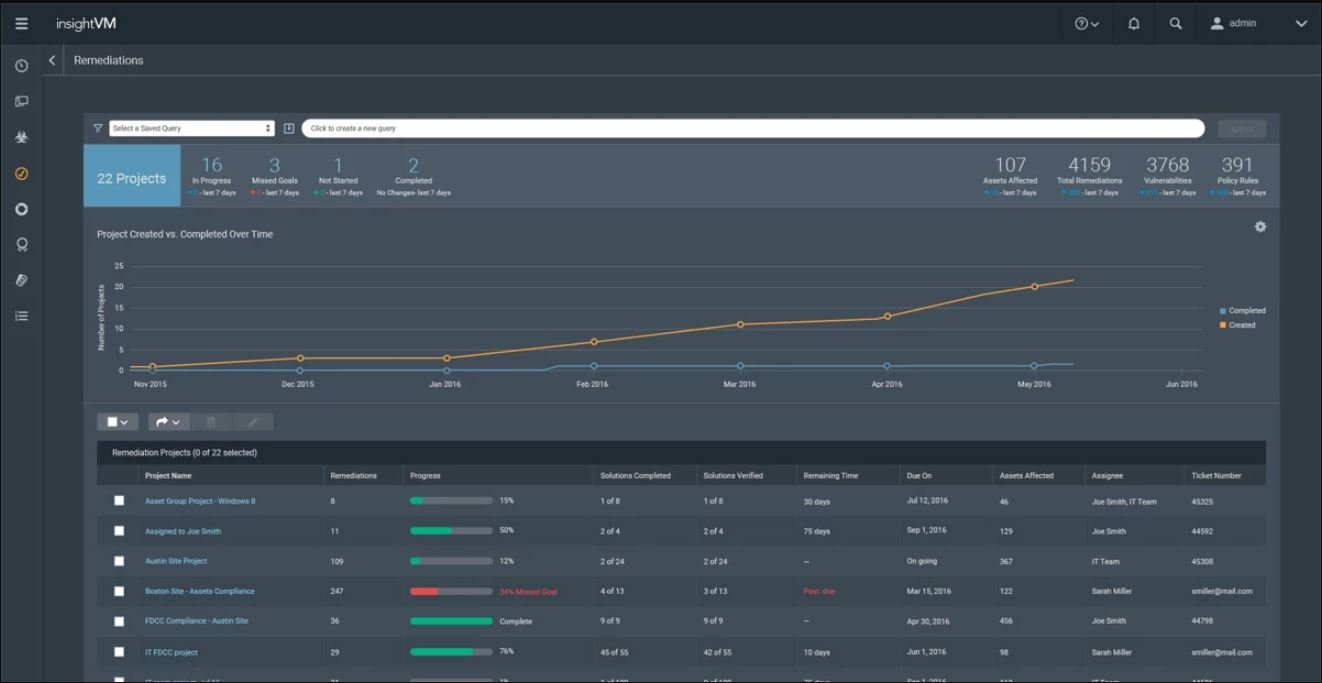
IT-Integrated Remediation Projects
-
Attack Surface Monitoring with Project Sonar
-
Integrated Threat Feeds
-
Goals and SLAs
-
Easy-to-Use RESTful API
-
Policy Assessment
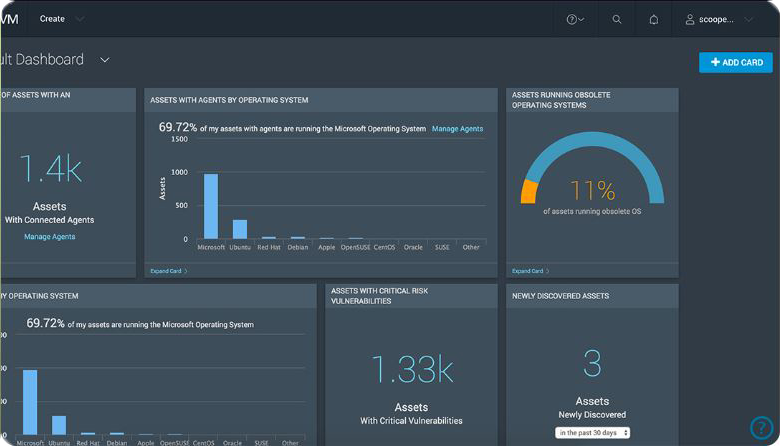
Understand and Prioritize Risk with Clarity
InsightVM not only provides visibility into the vulnerabilities in your on-prem IT environment and remote endpoints but also clarity into how those vulnerabilities translate into business risk and which are most likely to be targeted by attackers.
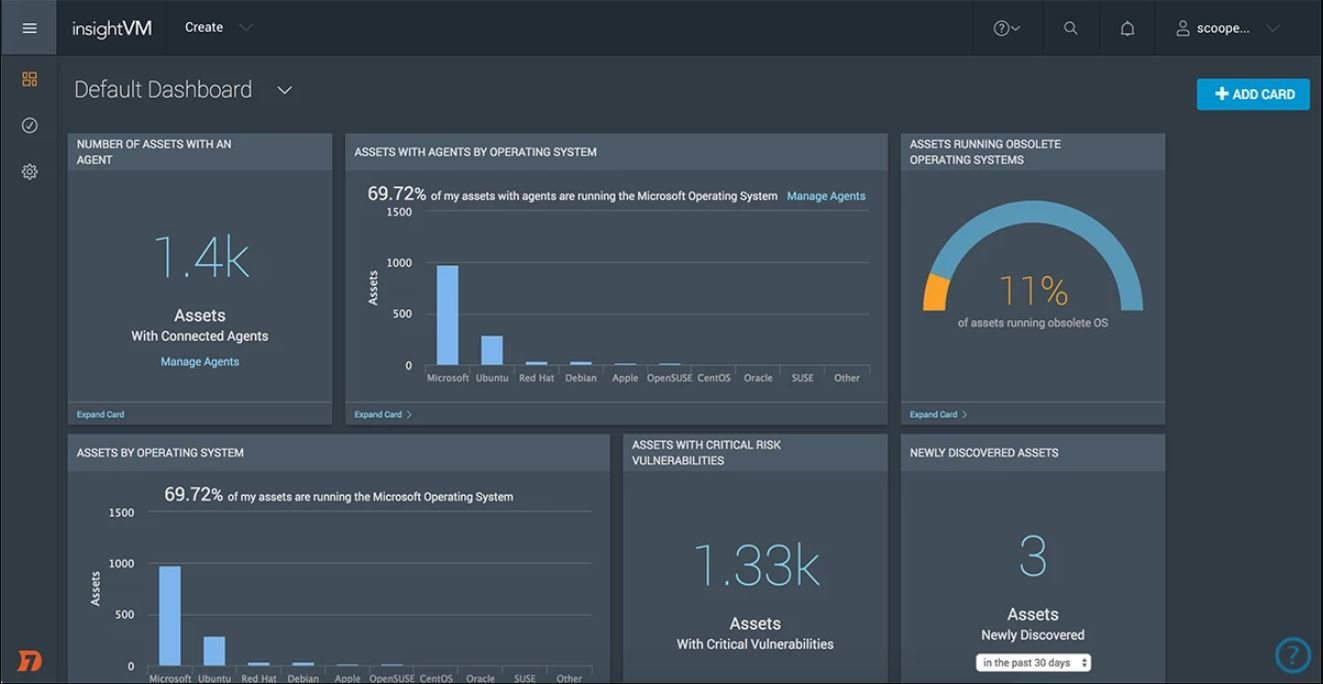
Remediate with Impact and Influence
InsightVM is not a silver bullet. Instead, it provides the shared view and common language needed to align traditionally siloed teams and drive impact. It also supports a proactive approach to vulnerability management with tracking and metrics that create accountability for remediators, demonstrate impact across teams, and celebrate progress.
Unify Endpoint Assessment
The Insight Agent is a universal, lightweight agent that collects data for Rapid7 InsightVM, InsightIDR, and InsightOps. Deploy it once, and get live intel on both network and user risk on your endpoints.
Maximize the Value of Your Tech Stack
Point solutions are a thing of the past. Rapid7's dedicated integrations team ensures that InsightVM is a foundational source of intelligence for the rest of your security program, helping all your products, like InsightIDR, work better together to collectively improve ROI.
Metasploit features
COLLECT
Gather together the collective knowledge of a global security community to test your network and find your holes.
PRIORITIZE
Determine the most impactful vulnerabilities and focus on what matters most.
VERIFY
Verify likelihood and impact with real-world attacks, fix top exposures and check that they are patched.
Gather Attack Information
-
Get unparalleled access to real-world exploits via the Metasploit Framework, maintained by 100,000+ contributors and users.
- Filter out dangerous exploits to enable anyone to conduct a safe penetration test, regardless of experience.
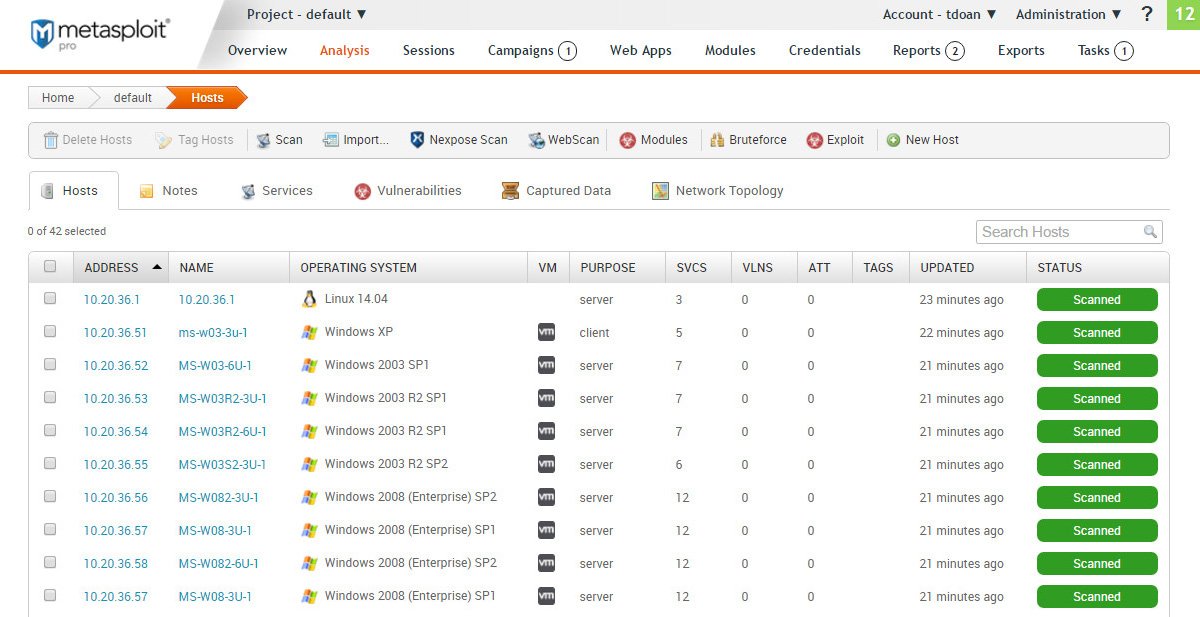
Prioritize Leading Attack Vectors
-
Integrate Metasploit with InsightVM to create the only closed-loop penetration testing and vulnerability management workflow and prioritize what matters most.
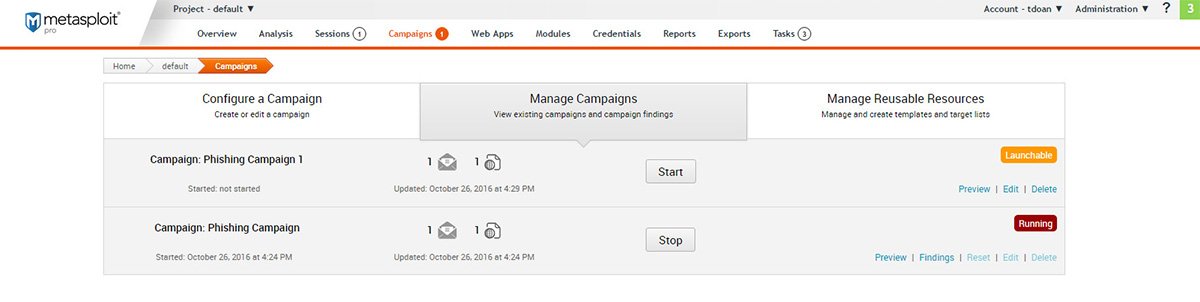
Remediate
-
Simulate every step in the kill chain to ensure your incident detection and response team can catch attackers at any stage.
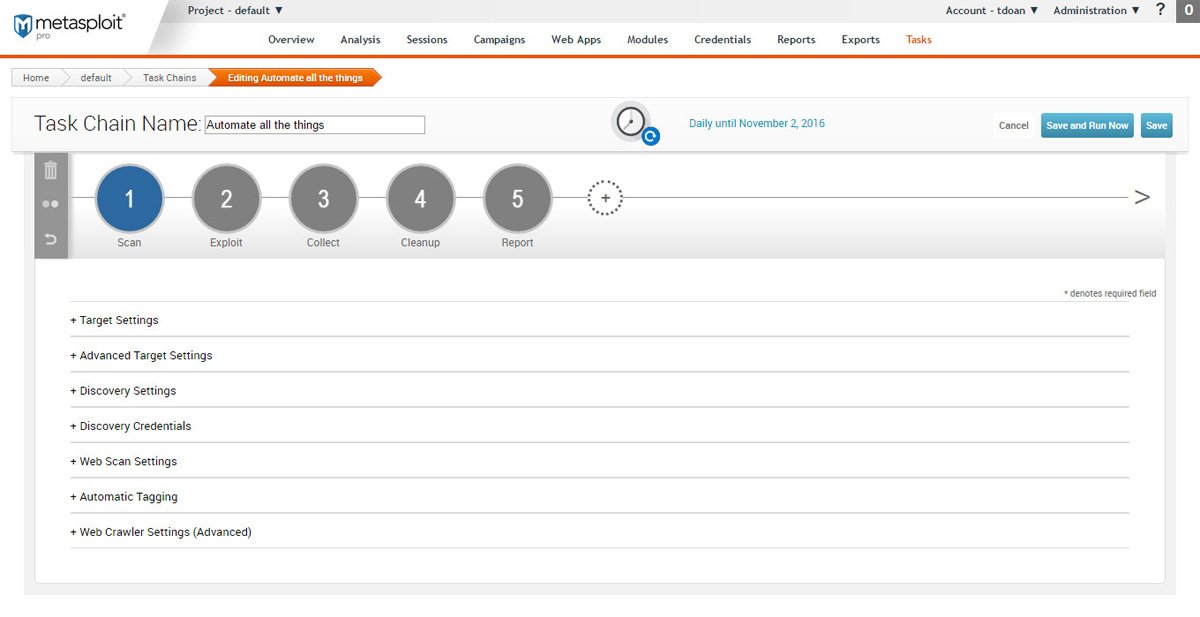
Send a price quotation request
Our specialist will contact you according to the request you sent, so please fill in the information accurately










